CEH | ComTIA Security + Certified | PHP Laravel Developer
Blog Grid
- Home
- Blog Grid
Types of Firewall

Types of Firewall
PACKET FILTERING FIREWALL
Packet filtering firewalls are security checkpoints that are connected to routers or switches. They monitor network traffic by filtering incoming packets based on their content. This helps to ensure that only authorized traffic is allowed through.
STATEFUL INSPECTION FIREWALL
Stateful inspection is a type of firewall that monitors the state of active connections. It uses this information to determine which network packets should be allowed through the firewall. To keep track of the connection state, it monitors the TCP three-way handshake.
STATEFUL MULTILAYER FIREWALL
Stateful multilayer is a type of packet-filtering firewall that examines all seven layers of the Open System Interconnection (OSI) model. This allows it to thoroughly examine each packet before allowing it through. Its advanced technology compares each packet to known states of friendly packets, ensuring that only authorized traffic is allowed through.
PROXY FIREWALL
A proxy firewall acts as a middleman between internal and external systems communicating over the internet. Its primary function is to protect the network by forwarding requests from the original client and masking them as its own.
NEXT-GEN FIREWALL
A next-generation firewall is a security device that combines several functions of other firewalls. It incorporates packet inspection, stateful inspection, and deep packet inspection to provide a higher level of security.
NETWORK ADDRESS TRANSLATION FIREWALL
NAT(Network Address Translation) firewalls are similar to proxy firewalls in that they act as intermediaries between a group of computers and outside traffic. They provide a private network that allows multiple devices with independent network addresses to connect to the internet using a single IP address. This provides an additional layer of security by hiding the internal network from external sources. When a device on the internal network requests access to the internet, the NAT firewall assigns it a temporary IP address that is used for communication with external sources. This helps to protect individual devices and the network as a whole from unauthorized access and attacks.
CIRCUIT LEVEL GATEWAY
Firewalls are crucial mechanisms for network security, and circuit-level gateways are a type of firewall that operates at the session layer of the OSI model. They are designed to mitigate the risk of unauthorized access to a network by observing TCP connections and sessions. Unlike packet filtering firewalls that inspect individual packets, circuit-level gateways rely on the TCP handshaking process to determine the legitimacy of a requested session.
CLOUD FIREWALL
A cloud firewall, also known as Firewall as a Service (FaaS), is a network security solution that operates in the cloud. It provides an additional layer of protection to networks by filtering incoming and outgoing traffic. Unlike traditional firewalls that are installed on-premises, cloud firewalls are managed and maintained by third-party cloud vendors.
APPLICATION GATEWAY FIREWALLS
Application gateway firewalls can inspect packets to ensure they meet application specifications. These firewalls are designed to protect web applications from malicious traffic, including common web application attacks like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). In addition to enhancing security, application gateway firewalls can improve application performance by caching frequently accessed content and offloading SSL processing from application servers.
application gateway firewalls are a valuable tool for protecting web applications and improving their performance. They provide granular control over network traffic, filter traffic based on specific application requirements, and help prevent common web application attacks.
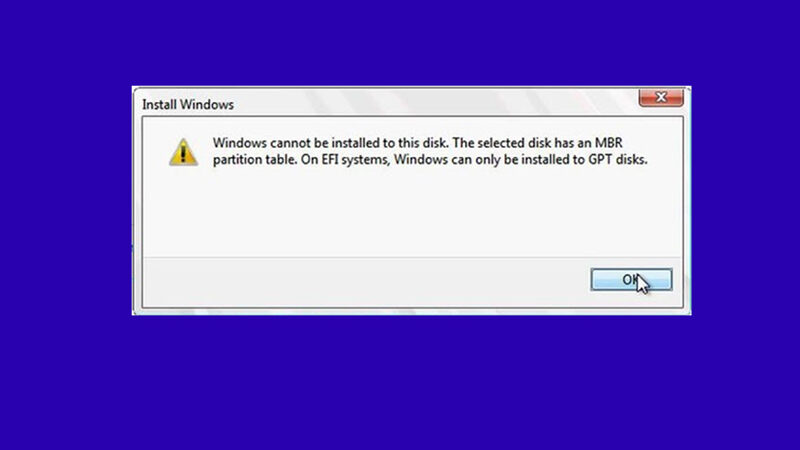
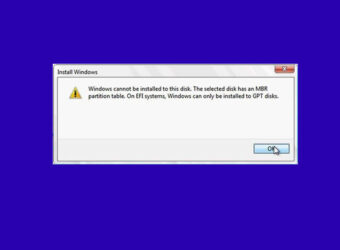
Solved: MBR GPT issue while installing windows
Have trouble installing windows?
Follow these steps to get rid of it!!
- Check your installation device(USB) partition type.
- change your partition type for installation ( if it is MBR and you are getting a GPT error change it to GPT or vice-versa)
- Thats it!!! Start the installation again and you are all done.
How to change the partition type of the installation device(USB).
I use a simple tool RUFUS to create a bootable installation media(USB)
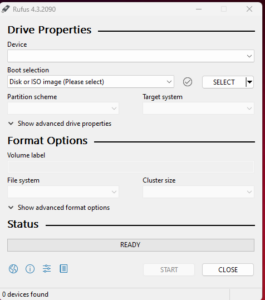
- Google it! download it! use it!
- Select your device i.e. USB drive where you are preparing your bootable installation USB.
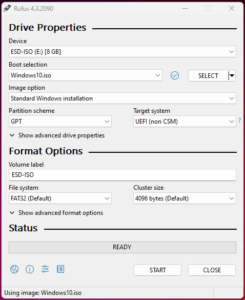
- change partition scheme for Device
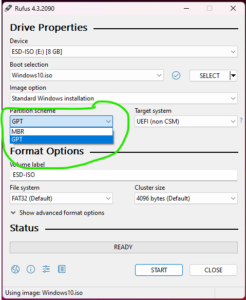
- You are all done.
- Try the installation again and have fun.
- Thanks
Phishing, Smishing and Vishing?

Phishing, Smishing and Vishing?
Phishing is a dangerous cyberattack that aims to steal your sensitive information by tricking you into clicking on fraudulent links in emails. Stay vigilant and cautious when opening emails and clicking on links. Cybercriminals often use sophisticated techniques to make their emails appear legitimate, but with the right knowledge and tools, you can stay protected and prevent these attacks. Stay informed and stay safe.
Smishing is similar to phishing but in the form of a text message that contains fraudulent links or downloads malware. These messages may appear as urgent requests from a bank or delivery service. Don’t fall for these scams, take the time to verify the authenticity of the message before sharing any personal information or clicking on any links. Stay informed and stay safe!
Vishing is a fraud that involves scammers calling and impersonating a legitimate company to steal personal info. They may ask for your name, address, driver’s license number, SSN, or credit card information. Some may even record your voice to use it to authorize charges or access your accounts. Be cautious, and verify the caller’s identity before sharing sensitive information. Stay informed and stay safe.

Safeguard yourself from online fraud with these steps.
- Never click on links from unknown sources. Verify notifications by navigating directly to the organization’s website.
- Don’t give personal information to unsolicited callers or emails. Hang up and call back using the official phone number listed on the organization’s website.
- Avoid answering calls or texts from unfamiliar numbers. Stay vigilant against online fraud.
Safeguard your password

Safeguard your password
To ensure your accounts are secure, it’s essential to strengthen your passwords by following these tips:
- Make it complex – try combining uppercase and lowercase letters, numbers, and symbols to create a strong password.
- No repeats – avoid using the same password across multiple accounts.
- Go long – aim for a minimum of 12 characters in length.
- No easy guesses – avoid using easily guessable information like your name or birthday.
- Use two-factor authentication (2FA) to add an extra layer of protection to your accounts.
Remember, consistency is vital to maintaining good password hygiene. Keep your passwords strong and secure!